AWS is one of the greatest things since sliced bread. It empowers engineers to get things done quickly by enabling them to take control of the steering wheel and drive. With a simple AWS account, engineers can create resources, update security groups, and deploy their applications in rapid-fire fashion. The ease and power of AWS might make it seem like a security nightmare, but it’s actually the opposite. AWS provides the tools and controls to ensure everyone is following best practices, allows to you achieve a hardened security posture, and take compliance to a level that was never even thought possible before AWS: continuously.
Blessing in Disguise
The dynamic nature of the AWS Cloud is a security blessing in disguise. I’ll explain.
The typical audit process can sometimes take months. By the time the process is completed, things have already changed 🤦🏻♂️ With AWS, things are so dynamically that the standard auditing process does not suffice. Instead, we need to ensure that our AWS account is compliant in real-time.
Let’s think about this for a moment. Isn’t better compliance something we want anyway? Or are we okay having our AWS account being compliant only briefly during the audit review? Or do we want to have our AWS account compliant all the time?
The answer is: of course all the time. Continuous compliance is a goal we should all strive for. We probably shy away from the goal because it sounds like an impossible feat. But is it?
It is entirely possible thanks to the powerful automation tools that AWS provides. The tools make continuous compliance not only possible but, dare I say, simple.
Meet AWS Config
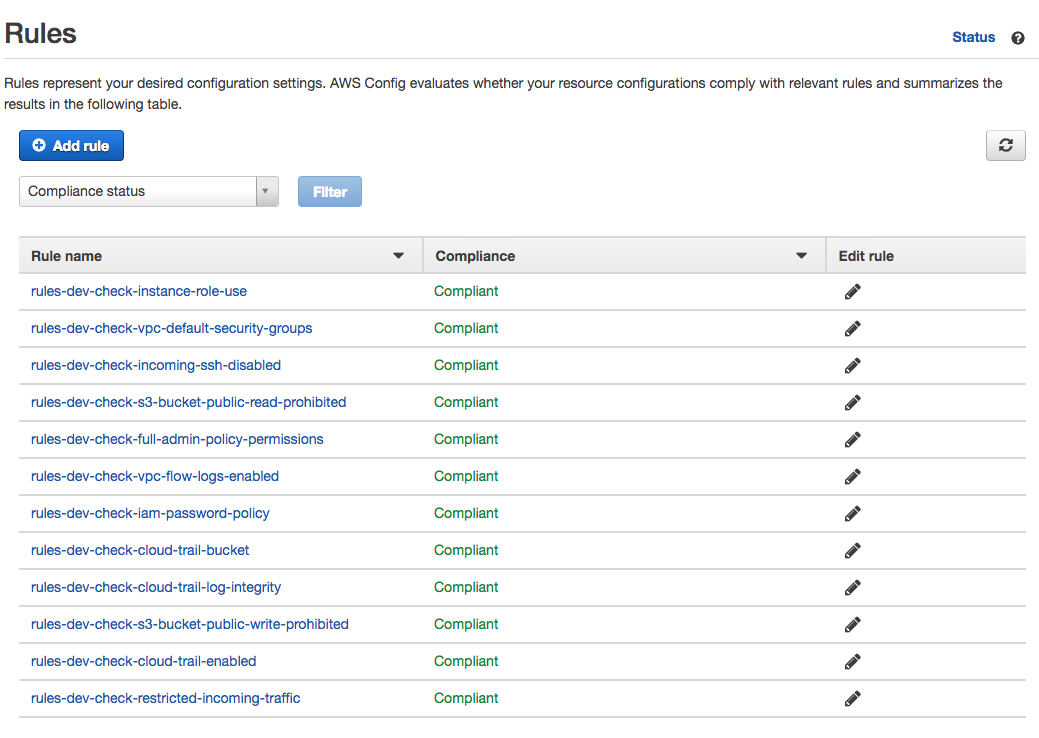
AWS Config is a service that allows you to show that your AWS account is compliant and prove it, continuously. It evaluates “rules” that you define according to your business requirements and tells you when the AWS account is not following those rules immediately. The dashboard looks like this:
The architecture of AWS Config rules looks something like this:
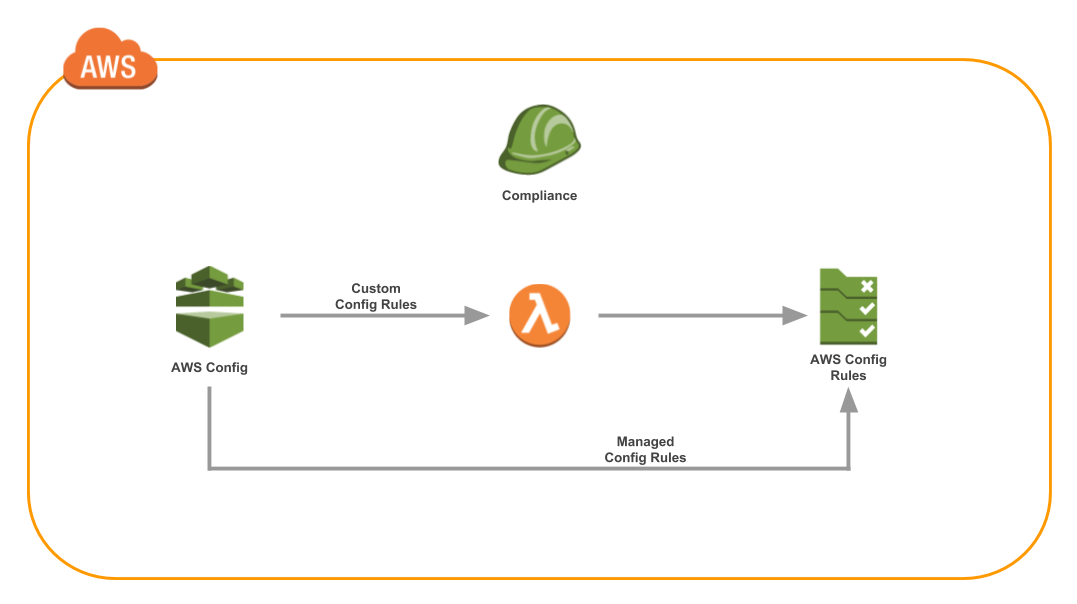
There are two types of Config Rules:
AWS managed rules are prebuilt and managed by AWS themselves. AWS maintains and updates the rules for you, which is helpful. You can customize managed rules with input parameters.
Custom rules are associated with AWS Lambda function and can be fully customized to meet your needs. They are useful when the managed rules don’t do quite what you require. This is where you tap into the power of AWS Lambda and serverless. You can add any custom business logic and define your security and compliance posture.
In real life, you’ll use a combination of the two types of rules to achieve compliance according to your business requirements. AWS turns the compliance world upside on its head and puts it in the real-time world. Hope you found this brief introduction to AWS Config helpful. In the next article, Continuous Compliance AWS Config Rules Implementation, we’ll talk about how actually to implement AWS Config in a clean manner.



